
Wikipedia: UDP Flood Attack · Course Study Material: TCP vs UDP

When the attacker initiates a SYN Flood attack using the IP address of the

Figure 3 Data flow with UDP Flooding and IRDP

But in a SYN flood attack, the attacker sends multiple SYN requests to the

works on the basis of a UDP flood attack (see Denial of Service Methods.

This is how I identified the UDP flood attack, normally my network will not

Rising botnet protection can detect flood attacks with SYN (synchronize)

IP launched UDP flood attack, and the time of the attack was stopped.

Rising botnet protection can detect flood attacks with SYN (synchronize)

HCFlood PUB. Edition - DoS - UDP Flooding Tool - Take down People + DOWNLOAD

You can view the number of UDP flood attacks and the number of dropped UDP

Figure 35: UDP Flooding

This device was blocking a 1.3GBit/sec UDP flood and was currently only

This Network Tool Comes With a UDP FLood, Pinger, Local Ip, Few More.
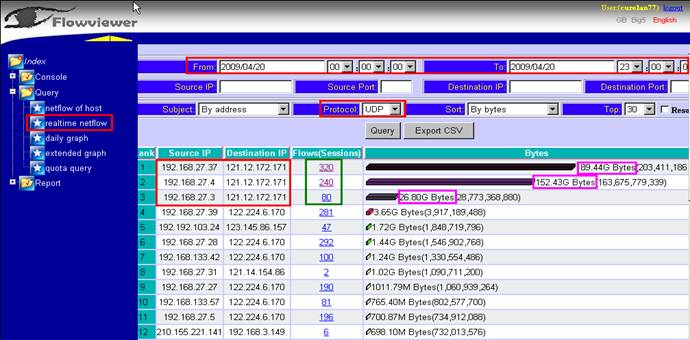
UDP Flood Attack. Following is the figure of the detecting result by

packet flood generators, ranging from general purpose (UDP flood,

Combine Attack: SYN+UDP Flood IACMP +TCP Flood UDP Small+TCP Connect
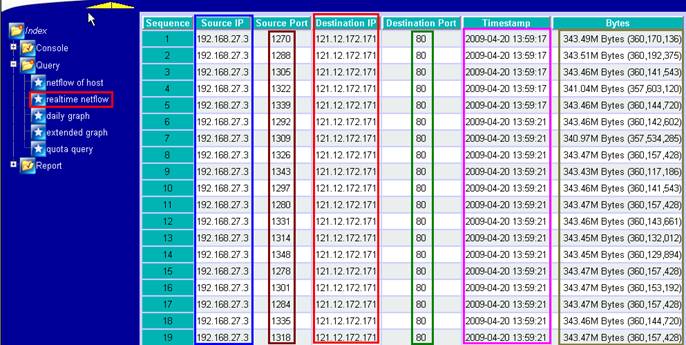
192.168.27.4 had infected and launch UDP Flood Attack to 121.12.172.171.

Radim Marek: Amazon EC2 still vulnerable to UDP flood attacks;

Step1 In the Attack Prevention Policy section, specify the protection action to be taken upon detection of a UDP flood attack.

No comments:
Post a Comment